Document Verification – Background
Digitization is taking off in a big way. The number of smartphone users has increased to around 2.9 billion in 2020 and more customers are demanding digital channels for services.
Nearly 40% of customers are more likely to obtain services from businesses that offer some sort of remote channel and businesses are now adapting to these new demands.
The new digital paradigm demands a revamp in how businesses implement KYC (Know Your Customer) protocols. This is especially true for financial institutions (FIs), which are usually heavily regulated to ensure that due diligence measures are followed.
With these factors in mind, regulators & FIs have had to redefine what it means to verify a customer’s identity.
According to the protocols of SCA (Strong Customer Authentication), a set of regulatory requirements under the EU Revised Directive on Payment Services (PSD2), comprehensive customer identity verification involves the authentication of the following elements –
- What only the customer can know
This involves verifying customer identity using something that only the customer knows, such as a password, pin, OTP, etc.
- What only the customer possesses
This involves verifying something that only the customer possesses, such as an identifying document like a PAN card, Aadhaar, Passport, etc.
- What only the customer is
This involves verifying a characteristic that is physically inherent to the customer. Examples include biometric verification, keyboard type patterns, iris recognition, facial matching, etc.
Document verification, therefore, is an integral tool in verifying a customer’s identity, whether it be during KYC verification for opening an account, investor verification before onboarding or vendor onboarding in retail.
Document verification, when conducted digitally, is referred to as digital document verification, as opposed to regular verification, which involves the manual cross-checking of details on paper documents.
Now that we’ve covered where the idea of document verification comes from & what it is, let’s take a brief look at what it involves.
The Basics of ID Verification
In order to verify an ID, the ID must first be issued to the customer. Once an ID has been issued, it can then be verified by the issuer (or account grantor) either independently or with assistance from third-party service providers.
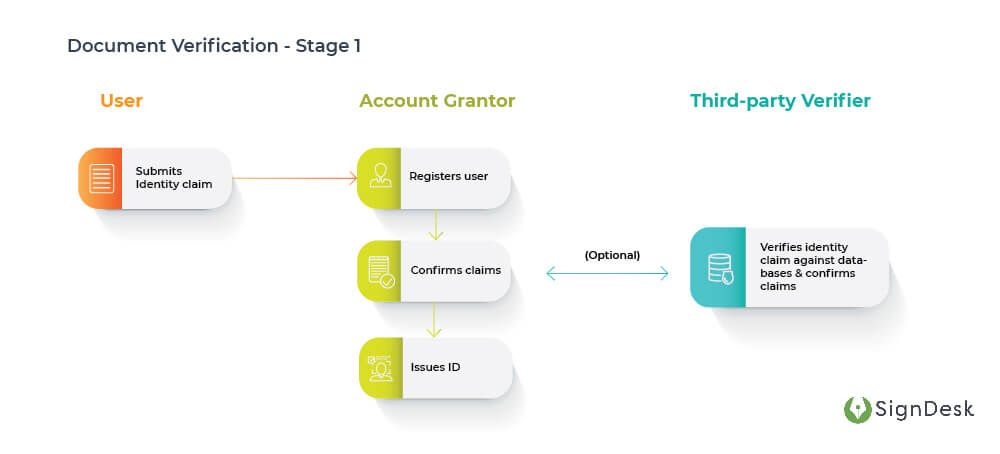
Let’s take a look at the first stage involved in ID verification.
In this stage, an entity (usually an arm of the government), registers a user after that user has submitted an identity claim, either creates a record using the identifying information supplied by the user or verifies this information against pre-existing databases, and then issues an ID.
Document Verification – Stage 1
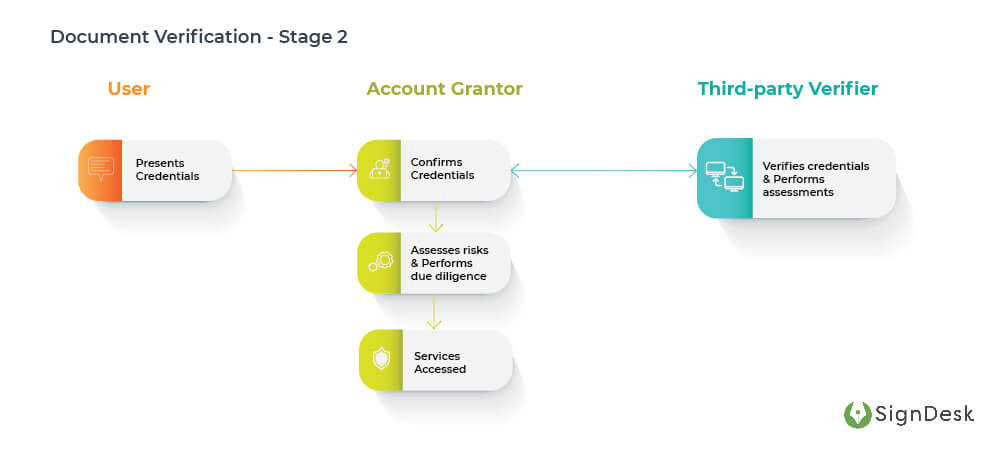
The second stage is where the actual “verification” part comes in.
In this stage, the account grantor is no longer a bureaucratic entity, but a regulated one. These include banks, NBFCs, insurers, securities firms & so forth. Here, the user submits pre-existing & trusted credentials to the account grantor. These credentials are then confirmed after the requisite risk assessments & fraud checks are completed, and the user is granted access to services.
Document Verification – Stage 2
Once these two stages have been successfully completed, the customer’s documents are verified.
These steps appear to be simple enough, but lacunae and weaknesses in the procedures involved in document verification leave it vulnerable for exploitation by bad actors & malevolent entities. This is equally true for digital document verification, where criminals employ various techniques to conduct identity fraud.
Identity Fraud: A Ubiquitous Threat
Identity fraud is when a party intent on misuse obtains access to certain crucial information about a person, and proceeds to use that information to falsely verify themselves & consequently obtain financial gain.
The keyword to notice here is the word “verify”.
Fraudsters indulging in identity fraud game the system to pass off someone else’s identity as their own, and once they’ve been cleared by the system these same fraudsters either take loans, apply for credit or open false accounts in the name of the person whose identifying credentials they’ve obtained.
But how do these criminals obtain this identifying information which, as we’ve seen, should ideally be something that only one person (the person this information belongs to!) has access to?
Two words – Data breaches.
Over the past year, we’ve seen numerous high-profile data breaches come to light. Several large businesses with massive customer records, including T Mobile, Pfizer, Warner Music Group, Barnes and Noble, Twitter, Cognizant, Zoom & Go Daddy, have experienced data breaches in 2020.
2020 has also seen a 141% increasein the volume records exposed online, a number which stands at nearly 37 billion.
With digitization taking off due to the conditions of COVID-19, more people are online for longer, and more information is available online; dovetail this with the fact that digital literacy is low for the majority of people in the world, and you’ve got a recipe for dire consequences.
These consequences are already a reality for a lot of financial institutions.Fraud losses are up by 13% in 2020, and USD 16.9 billion has been lost to fraud in the previous year.
In South Asia, online fraud is up by 65%, and 28% of all fraud cases involve identity fraud, according to reports.
Financial institutions, therefore, must preemptively take steps to protect every stage of the information collection process from hackers, and this includes document verification, which is where the majority of information is collected.
In order to better combat ID fraud, it’s imperative to learn more about it. First, let’s take a look at what the different types of fake IDs in circulation are.
What are the various types of fraudulent IDs?
Fake IDs, incidentally, come in all sorts of shapes and sizes. However, they can be classified into the following categories.
- Forged IDs
These are IDs on which some information has been illegally changed, in order to modify the identity of the ID holder. This could involve –
-
- Changing the variable information
- Inserting real pages from another ID
- Removing pages or specific information
- Applying false stamps or watermarks
- Digitally altering or adding information on an image of an original ID
- Counterfeit IDs
This is the total reproduction of an entire ID, in which the fraudster will obtain a template of the ID and insert their own information.
- Stolen blank IDs
These are non-personalized blank IDs stolen from the supply chain. Fraudsters then insert their own information into the ID.
- Illegally obtained genuine IDs
These are IDs obtained after supplying authorities with false information. This information could involve photos of someone else, fake personal details or fake verifying documents.
- Camouflaged IDs
These are rare cases in which fraudsters create issuing authorities that either does not exist or are not allowed to issue IDs.
- Imposter IDs
In such cases, the ID itself is original but is used by someone who isn’t the legal holder of the ID.
- Compromised or sample IDs
These are legally valid IDs that are available online either as sample IDs or as compromised IDs that have been exposed by hackers or thieves.
The most common of these fraudulent IDs are forged & counterfeit IDs, which have been created using information illegally obtained through data breaches or on the dark web.
This covers all the fake IDs present in the market. But how worried should FIs be about the threat posed by this?
Measuring the Threat of Identity Fraud
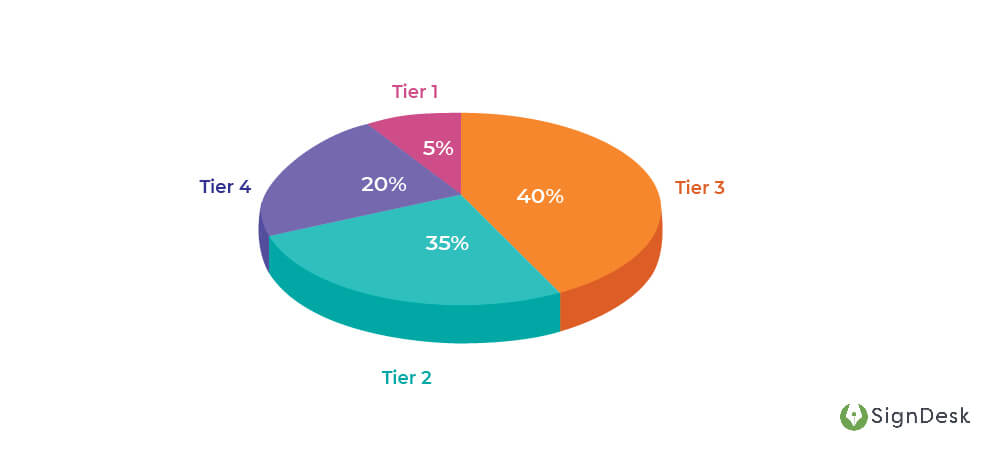
Identity fraud can be classified into four different tiers based on the level of sophistication involved in the fraud. These levels are inversely proportional to their threat level to FIs.
- Tier 4
These are unsophisticated & dilettantish attempts at identity fraud. Tier 4 ID fraud typically involves camouflaged IDs that are easily detectable.
Tier 4 ID frauds make up 20% of all ID fraud instances.
- Tier 3
These involve poorly manufactured or slightly altered ID templates that have been filled with fake information. These cases of fraud are detectable by examining data format & consistency criteria.
Tier 3 frauds make up 40% of all instances of ID fraud.
- Tier 2
These are largely sophisticated attempts at ID fraud. In Tier 2 cases, the data present is verifiable; however, there are small & machine-detectable variations in font, layout & security features.
Tier 4 frauds make up 35% of ID fraud cases.
- Tier 1
These are the most sophisticated & dangerous attempts at ID fraud. In these instances, the supply chain is compromised to obtain blank IDs, and genuine IDs are obtained through social engineering or the black market.
5% of all ID fraud cases are Tier 1 frauds.
ID Fraud Distribution:
Now that we’ve examined the range of ID fraud cases, let’s take a look at how ID fraud is detected.
How to Detect ID Fraud
While the number of cases of ID fraud have been skyrocketing, the other side hasn’t been sitting idle. Government-issued IDs usually all have specific layouts, designs & built-in features that allow verifiers to determine the authenticity of an ID.
The techniques used to detect ID fraud are numerous, but they can all be classified into the following categories.
Data Integrity Analytics
These techniques evaluate the integrity of the text & numerical fields present in the ID. Some of the techniques used in data integrity analysis include –
- Data Validations
In this technique, the original ID template is used to determine whether valid data is present in specific formats in all areas in the ID and the MRZ (Machine Readable Zone).
For example: The MRZ in an Indian Passport contains the name, passport number & date of birth of the passport holder. These data can be validated to make sure that the passport is authentic.
- Algorithmic Validations
Some IDs include specific rules, in the form of mathematical algorithms to identify any flaws in the ID. These rules are followed during the creation of the ID & therefore can be coded into an ID checker system to validate the authenticity of an ID.
For example: PAN cards follow very specific rules when it comes to the data present on the card –
- The first 3 characters are alphabets between A-Z
- The fourth character indicates the type of cardholder
- The fifth character is the first letter of the last name of the card holder
These rules can be used algorithmically to check whether an ID is fake.
- Data Consistency
Certain data present in multiple locations & multiple formats on the ID must match. Some IDs even have machine-readable text encoded with this information, which when decoded will indicate the requisite data. Data consistency checks are a useful tool to determine the validity of an ID.
For example: The Indian passport, as mentioned before, contains an MRZ with data that repeats in other parts of the passport. Verifying the MRZ, therefore, is an example of a data consistency check.
- NFC Chips
NFC (Near-field communication) chips enable short-range communication between two devices and contain additional verifying information that can be read by specific devices. This information can then be compared to the information appearing on the ID & matched to authenticate the ID’s validity.
Visual Document Authenticity
These are techniques that can be used to validate IDs using scanned images of the ID. They can be classified as –
- Document Template Comparison
All government-issued IDs have templates with spatial & design-based specifications. An ID can be visually compared to its template to determine certain geometric inconsistencies that can determine whether the ID is fraudulent.
- Digital Tampering
The software can be used by fraudsters to digitally manipulate IDs by replacing certain information or changing the picture in the ID. However, these software leave trails that can be caught. For example, the pixels in the ID image can be analyzed by KYC verification software to determine whether the ID has been tampered with.
- Font Anomalies
When an ID has been digitally manipulated, fraudsters will leave certain font anomalies that can be caught by KYC verification software.
- Security Features
Numerous IDs have security features in place such as digital watermarks, embossed text & barcodes which can be used to validate the authenticity of an ID.
Proof of Ownership
The proof of ownership of an ID can be determined conclusively via facial matching techniques. The latest KYC verification software takes a live picture or selfie of the current ID holder and matches it with the picture in the ID to ensure that the current ID holder is the same as the original ID holder.
These are a few of the techniques used by verifiers to determine whether an ID is fake. Now let’s look at how digital document verification works in real life.
Real-time Document Verification – How it works
Real-time document verification uses most of the techniques mentioned above to authenticate documents to a high degree of accuracy.
SignDesk’s KYC verification solution employs AI-powered ID verification techniques to digitally validate nearly all government-issued IDs including PAN card, Aadhaar, Passport, Voter ID, GSTIN & Driving Licence.
Here’s how SignDesk’s ID verification works –
- A scanned image or photograph of the ID is uploaded onto the dashboard
- OCR technology is used to convert the details on the ID to machine-readable text & the relevant details are extracted
- Data integrity analysis & visual document authentication are used to validate the extracted details
- All details are validated using standard databases
- If the match percentage is greater than a certain threshold value, the document is successfully validated
- A live image of the customer is captured & matched with the photo on the ID to ensure proof of ownership
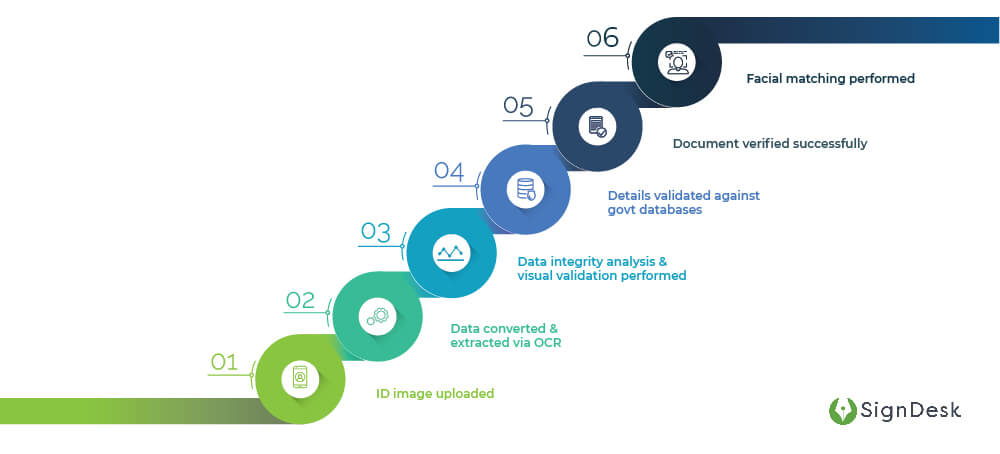
This entire process takes just a few minutes to complete & is completely digital. Validation is carried out successfully in the majority of cases & does not require any physical intervention. These are just a few of the advantages of digital document verification. Here are some more.
Why choose Digital Document Verification
Nearly 93% of businessesin the financial sector have a “digital-first” strategy in place & 56% of CEOs say that digital improvements have led to increasing in revenue. Digitization, therefore, is here to stay.
Digital document verification significantly reduces operational time & costs, resulting in several benefits for businesses in general & FIs in particular.
Here are some reasons why FIs need to get onboard with digital document verification.
- Reduced expenses
Digitization has been shown to reduce operational expensesfor businesses by between 50-85%. Automating the KYC verification process using AI, OCR verification & ML techniques also increases ROI by at least 5x.
- Secure & fraud-proof
Banks & insurers have lost billions to frauds over the past year. Digital document verification secures the KYC process using a host of verification techniques & uses ML-based filters, among other techniques, to filter out fraudulent profiles & fake IDs.
- Shorter turnaround times
Automating the KYC verification process reduces TAT on account opening, loan disbursement & other processes by upto 99%. AI-powered document verification has helped SignDesk’s clients reduce TAT from 10-20 days to a mere 10 minutes.
- Fewer errors & zero information loss
Manual errors & misplaced documents are frequent issues when it comes to document verification for KYC. By automating the document verification process, FIs can ensure that there are no manual errors in the KYC process & that all customer-related information is safe on a digital platform.
- Increased customer satisfaction
Customers are increasingly demanding digital channels to obtain financial services. Surveysindicate that businesses providing a strong omnichannel experience retain on average 89% of their customers. Digital KYC verification also reduces KYC drop-offs by 20%.
Award-winning KYC Verification & Digital Onboarding
SignDesk is an award-winning provider of AI-powered verification and documentation solutions to businesses.
We use real-time AI-powered document verification techniques, OCR-enabled image data extraction, facial matching & ML-based fraud filters to automate and expedite the KYC verification process.
Our verification solutions have helped our 250+ clients reduce onboarding expenses, cut down on KYC drop-offs, reduce TAT by 99%, and safeguard against fraud using cutting-edge compliance technology.
Our efforts to automate KYC have been recognized in the form of numerous awards, the latest being the Best AI/ML Product at InnTech 2020, and the Global Banking & Finance Review’s Best Digital Onboarding Product of 2020.
Are you ready to join 50+ major banks and start onboarding with Video KYC? Book a demo with us now and let’s get started!